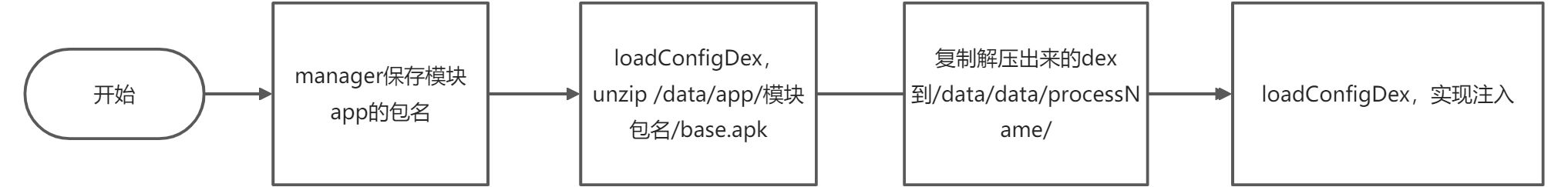
源码分析 manager 提供 ui,将配置信息存入 PackageItem 对象,并且塞入 packageList 集合
public class ConfigUtil {configPath =”/data/system/mik.conf”;breakConfigPath =”/data/system/break.conf”;sysHide =true;TAG =”MikManager”;
public static void SaveMikromConfig(List packageList){e (ConfigUtil.TAG ,”SaveMikromConfig”);getiMikRom ().writeFile(ConfigUtil.configPath ,savejson);e (ConfigUtil.TAG ,”writeConfig err:”+e.getMessage());
ROM 层进行读取
1 2 3 public static String getMikConfig(){ try { IMikRom mikrom=getiMikRom();
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 //注入dex public static void loadConfigDex(Application app){ String processName
dexClassLoader.loadClass()
1 2 3 4 if(System.getProperty("os.arch").indexOf("64") >= 0) {
copy libsandhook.so 到/data/data/PACKAGENAME//libsandhook.so
onStrat() 1 2 3 4 5 6 7 8 9 10 11 12 13 14 public void onStart(String path) { Log.e(TAG, "Inject onStart");
SandHookConfig.libSandHookPath = path; //设置 sandhook path
思路: